This post is a collation of articles and other references backing up a personal research about the current state of security of Philippine online banking portals. The purpose of this research is mainly educational and encouraging awareness of our online activities — one of which is online banking.
Disclaimer: I am no expert in Information Security or Cybersecurity and I have minimal technical knowledge of the aforementioned fields as of this typing. If you are an expert on any of these fields and you have any concerns or additional input, feel free to post on the comments section below.
The main goal for this research is to answer this question:
Is your online banking secure enough?
Cybersecurity, or security in general, is a cat-and-mouse chase. Each day, software vulnerabilities and security holes are found, reported, and patched. But sometimes, a mouse can outsmart the cat. Attackers can find and exploit these vulnerabilities before they could be known and fixed by a patch. The users of the system will always be the victims.
There are techniques and technologies that help secure a system. The crucial part to keeping a system secure is to always use the latest release of these technologies as most likely the reason for the release would be a security patch to fix a recently discovered vulnerability.
What happens when the system you are using does not follow this practice? Well, it is like sending an open invite to attackers.
For this research, I will make examples of banks I can think of while writing this. I will use Google Chrome for checking the details of my connection to the following online banking portals and Qualys SSL Labs scanner for a deeper review. Technologies such as encryption, cryptography, and protocols will be the main basis for this research.
UnionBank
The main portal for personal banking is under this domain: ebanking.unionbank.ph
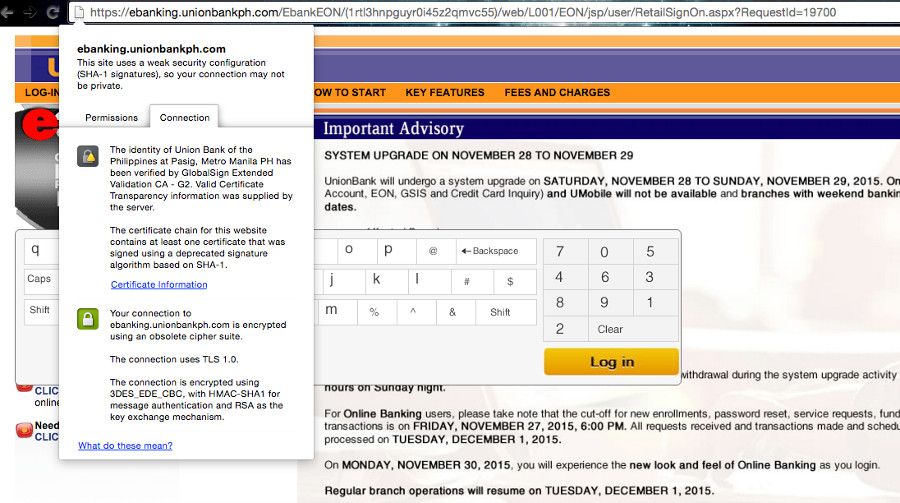
“This site uses a weak security configuration (SHA-1 signatures), so your connection may not be private.”
“The certificate chain for this website contains at least one certificate that was signed using a deprecated signature algorithm based on SHA-1.”
SHA-1 has been vulnerable since 2005. More info here and the full report on this document. Security experts recommend SHA-2 or SHA-3.
“Microsoft, Google and Mozilla have all announced that their respective browsers will stop accepting SHA-1 based SSL certificates by 2017 (and that SHA-1-based certificates should not be issued after 2015). In conclusion, our estimates imply SHA-1 collisions to be now (Fall 2015) within the resources of criminal syndicates, two years earlier than previously expected and one year before SHA-1 will be marked as unsafe in modern Internet browsers. This motivates our recommendations for industry standard SHA-1 to be retracted as soon as possible.” - The SHAppening: freestart collisions for SHA-1
“The connection uses TLS 1.0.”
TLS 1.0? Is there an acceptable reason why an online banking portal uses an older protocol? Funny how there’s a saying circulating the InfoSec community: “You don’t have to be a bank to upgrade your TLS implementation.” Perhaps, the ‘bank grade security’ IRL doesn’t apply online? Hmmm…
TLS 1.0 has been introduced in …wait for it… 1999! *badum-tss* The newer protocols are TLS 1.1 (released 2003) and TLS 1.2 (released 2008). And browsers started supporting TLS 1.2 since 2013 with almost all modern browsers supporting it by 2014. Why so behind? Just why?
UnionBank’s server also uses SSL 3. If you are not yet aware why this is a red flag, I’ll save the explanation for later on another bank who also implemented SSL 3. (Click me.)
“Your connection to ebanking.unionbankph.com is encrypted using an obsolete cipher suite.”
The server accepts the RC4 encryption algorithm by which multiple vulnerabilities are found and can be exploited by the following attacks:
- Fluhrer, Mantin and Shamir attack (2001)
- Klein’s attack (2005)
- Royal Holloway attack (2013)
- Bar-mitzvah attack (2015)
- NOMORE attack (2015)
I planned to save negative remarks to myself but dear lord — UnionBank’s server also supports 512-bit export suites — plain RSA. Any less than 2048-bit is considered weak. To put it bluntly, this is undoubtedly A VERY UNSECURED SITE. This obsolete cipher suite is obsolete for many reasons: one of them is being susceptible to the FREAK attack. “It allows an attacker to intercept HTTPS connections between vulnerable clients and servers and force them to use weakened encryption, which the attacker can break to steal or manipulate sensitive data.” Meaning, if an attacker knows you do online banking at UnionBank, they can act as a middleman between you and the website and do whatever they want with your data.
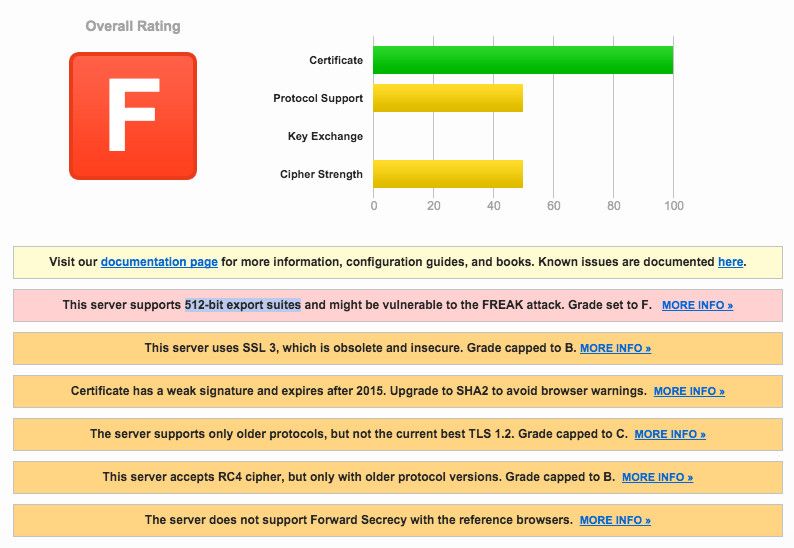
UnionBank Security: DANGER ZONE. [Full Report | Latest Scan]
Bank of the Philippine Islands
The main portal for personal banking is under this domain: secure1.bpiexpressonline.com
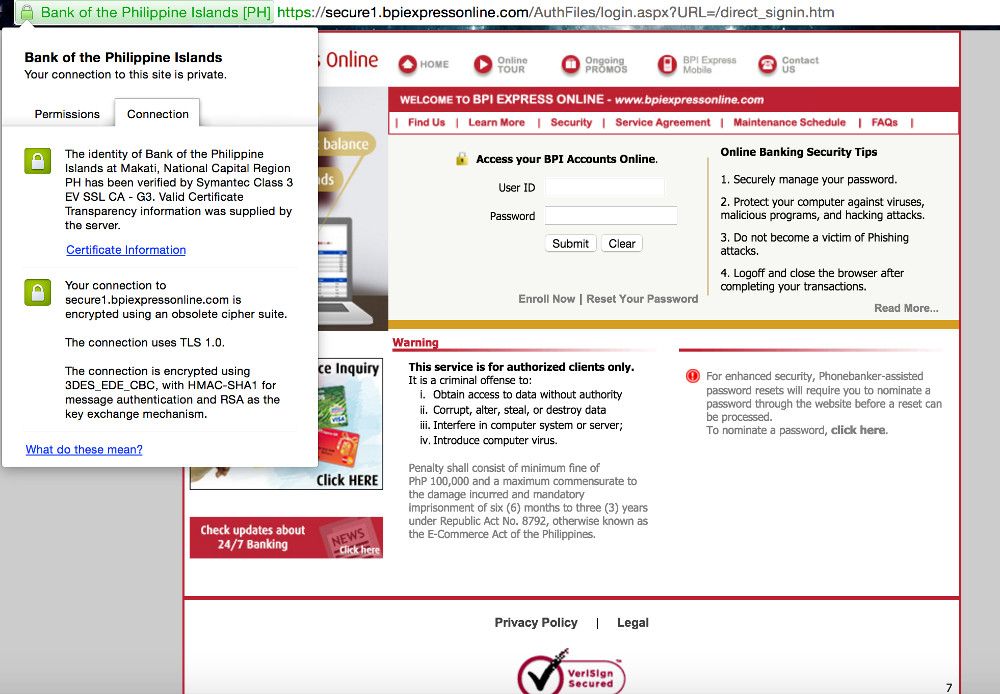
BPI uses the TLS 1.0 protocol using cipher block chaining (CBC) for encryption.
Again, the only secure protocol version is TLS 1.2. Older protocols have known vulnerabilities. TLS 1.0 using CBC-mode for encryption is open to the Lucky 13 attack. Their server also accepts the RC4 cipher for which, as I cited above, is vulnerable to a number of attacks since 2001.
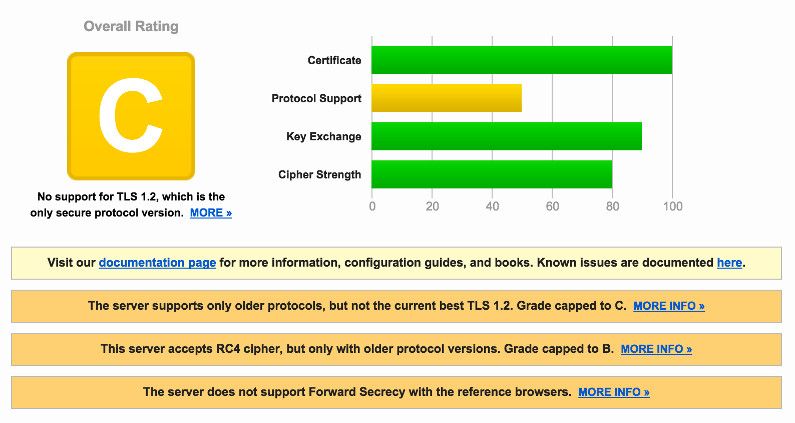
BPI Security: UNSECURED. [Full Report | Latest Scan]
Metrobank
The main portal for personal banking is under this domain: personal.metrobankdirect.com
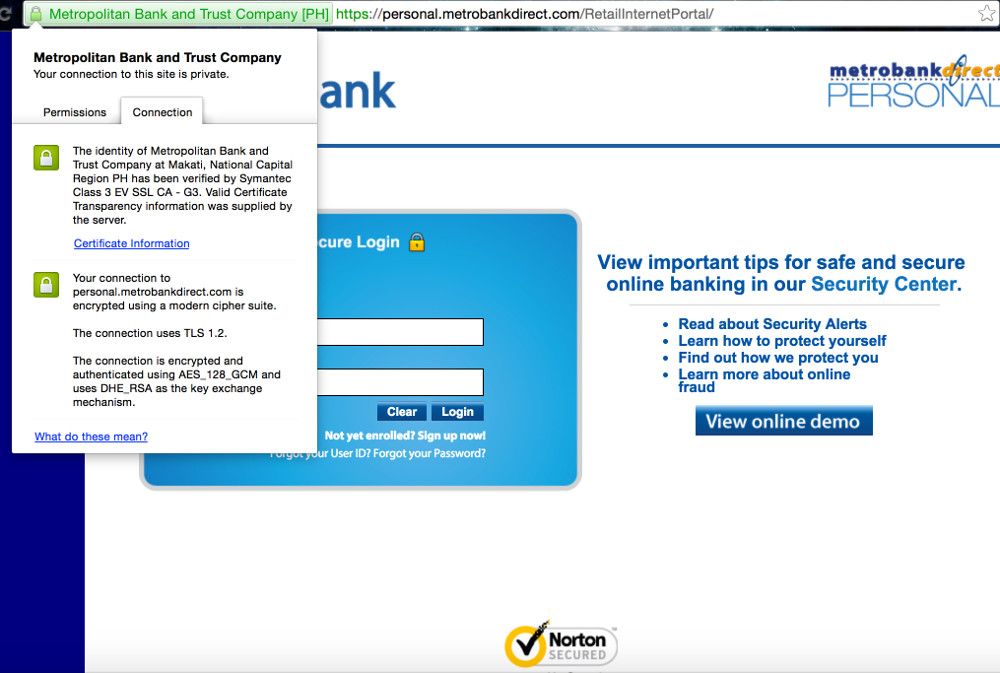
Good news, Metrobank users. As you can see on the screenshot, the site uses the latest protocol: TLS 1.2, a modern cipher suite: DHE_RSA with AES_128_GCM, and RSA 2048-bit key for encryption.
The Metrobank server supports Diffie-Hellman (DH) key exchange parameters where a weakness has been uncovered and is prone to the Logjam attack. “The Logjam attack allows a man-in-the-middle attacker to downgrade vulnerable TLS connections to 512-bit export-grade cryptography.” And as I mentioned above, any key lower than 2048 bits is weak. However, their server also supports TLS_FALLBACK_SCSV to prevent protocol downgrade attacks. Good job, Metrobank.
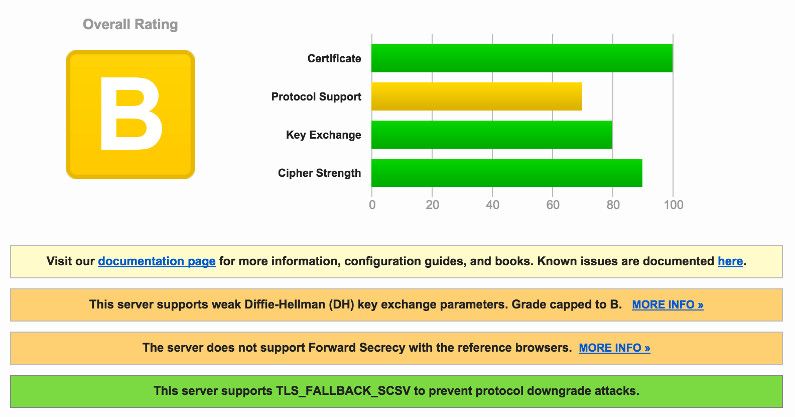
Metrobank Security: SECURE. [Full Report | Latest Scan]
EastWest Bank
The main portal for personal banking is under this domain: www.eastwestpersonal.com.ph
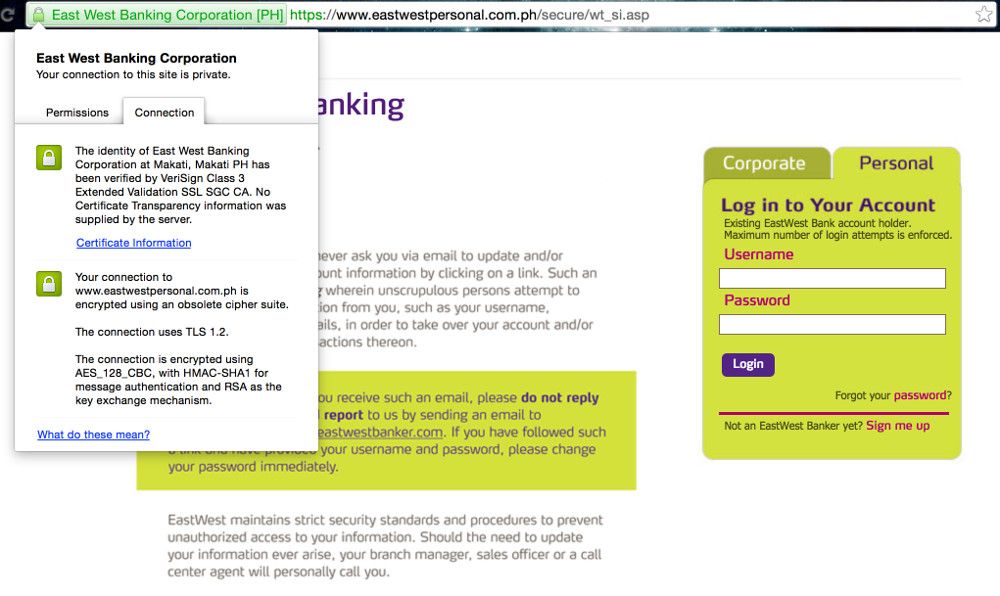
As you can see, EastWest Bank is using the latest protocol: TLS 1.2. Disappointingly, like UnionBank, they also use SSL 3, which is an 18-year-old obsolete technology. With the SSL 3 implementation, even with TLS 1.2, EastWest Bank’s banking portal is susceptible to the POODLE attack. “This vulnerability allows the plaintext of secure connections to be calculated by a network attacker.” Meaning, logging in on this site is unsafe. Attackers can steal your username and password and exploit your data. More info about the POODLE attack here. They SHOULD DISABLE SSL 3 on their servers as soon as possible. If disabling it is out of the picture for some reason, the remedy would be to implement the TLS_FALLBACK_SCSV mechanism like what Metrobank did.
They are also using SHA1 signatures with plain RSA as the encryption key in CBC-mode with RC4 cipher suite. And as I mentioned on the previous reviews, all vulnerable to known attacks.
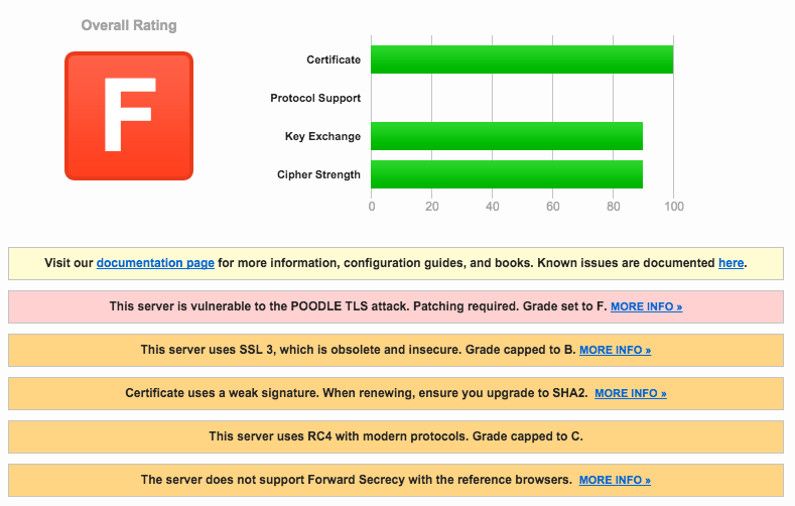
EastWest Bank Security: DANGER ZONE. [Full Report | Latest Scan]
Banco de Oro
The main portal for personal banking is under this domain: online.bdo.com.ph
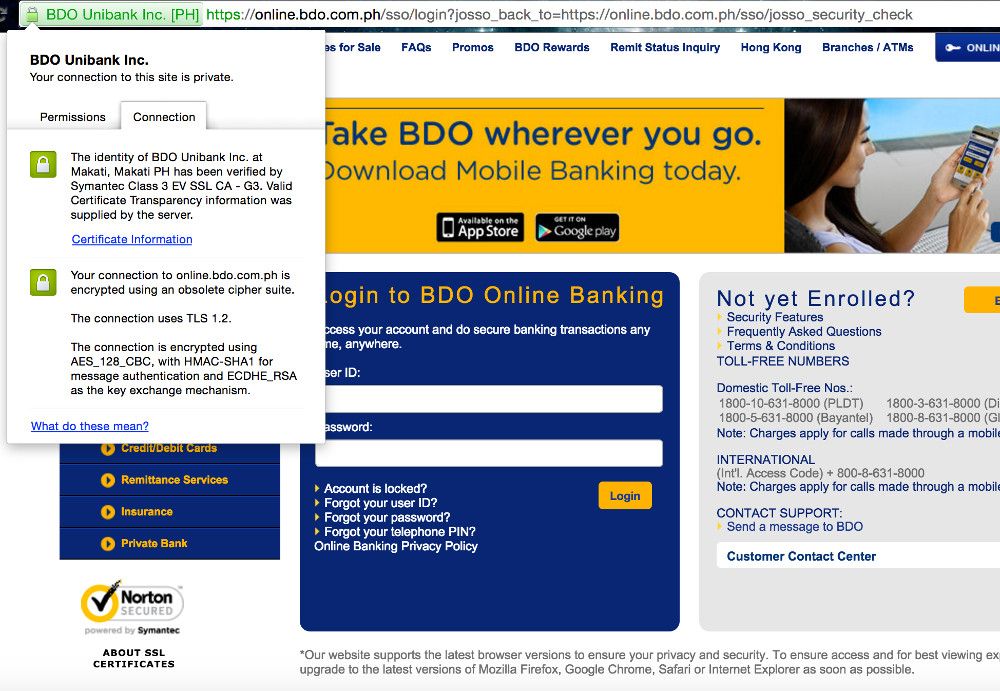
BDO is using the latest protocol: TLS 1.2 but Chrome reported that the site is encrypted using an obsolete cypher suite. The main trigger for this warning is the AES_128_CBC cipher.
On Chromium Security standards, ‘modern’ cryptography entails:
- TLS 1.2 (protocol)
- AES_128_GCM or CHACHA20_POLY1305 (cipher suites)
- DHE_RSA or ECDHE_RSA or ECDHE_ECDSA (key exchange)
Related link: Google Chrome “Your connection to website is encrypted with obsolete cryptography” on Information Security StackExchange
Notice the difference on the second item: CBC refers to cipher block chaining and GCM to Galois/Counter Mode.
GCM is another mode of operation that is an authenticated encryption algorithm while CBC is a common mode.
And as previously mentioned, CBC-mode in TLS 1.0 is susceptible to the Lucky 13 attack. However, another variation of the POODLE bug has been uncovered late 2014 that also affected TLS implementations with CBC-mode encryption. TLS 1.2 is reported safe from this attack.
As an additional layer of security, BDO also supports TLS_FALLBACK_SCSV.
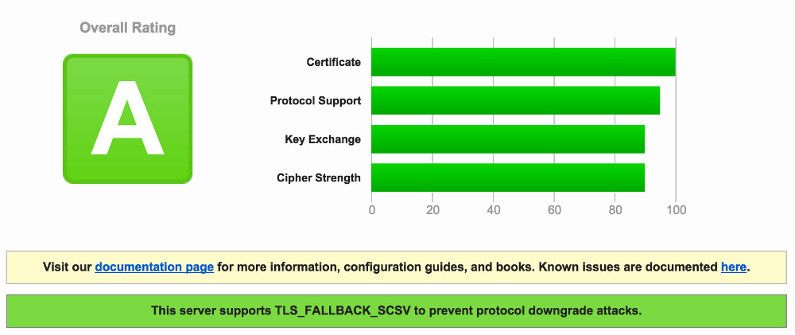
BDO Bank Security: SAFE AND SECURE. [Full Report | Latest Scan]
In summary:
Two banks are graded SECURE: Metrobank and Banco de Oro — Safe to use for online banking.
One bank is graded UNSECURED: Bank of the Philippine Islands — Use caution when entering sensitive data.
Two banks are graded as DANGER ZONES: Unionbank and EastWest Bank — Not safe to use.
If you have questions, objections, requests, suggestions, or concerns, feel free to start a discussion on the comments section below.
Be safe online.